상단 정보영역
Information Protection
strives to manage and protect it safely by complying with laws and guidelines related to information protection such as the Personal Information Protection Act.
Information Protection Policy
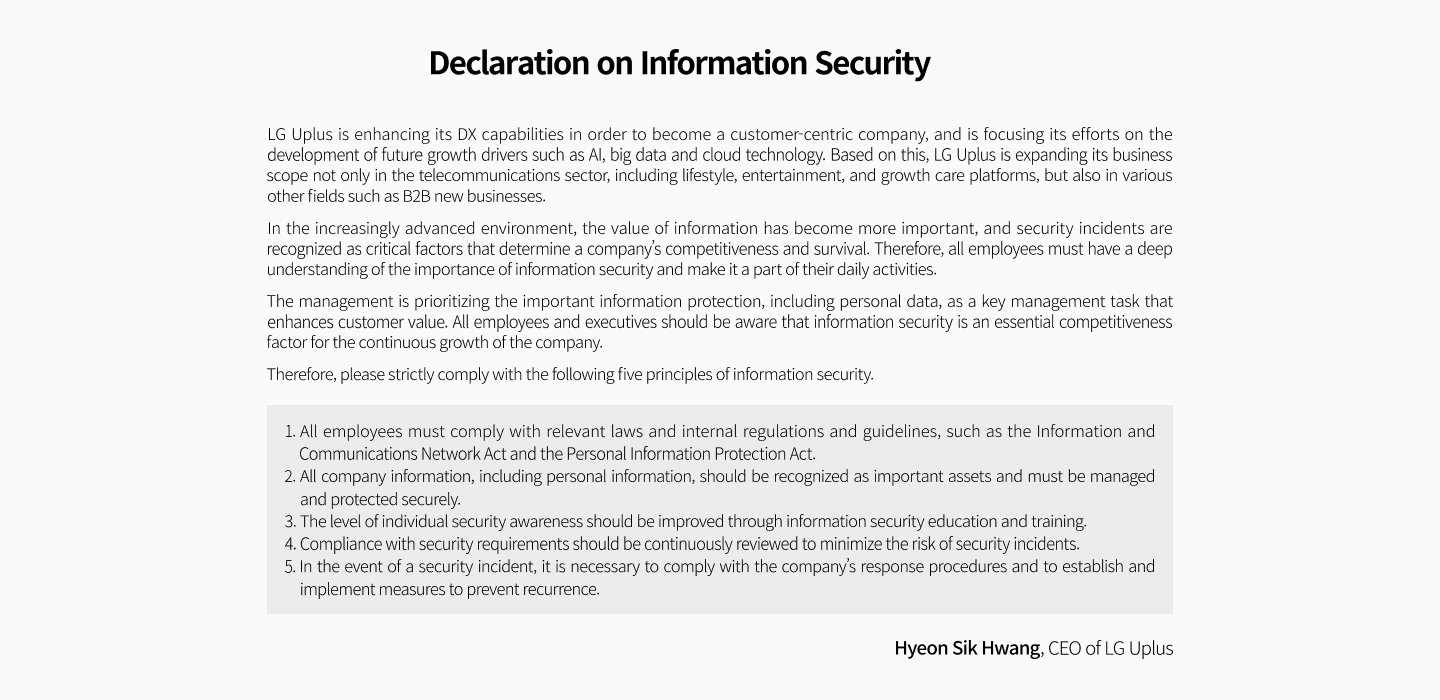
Declaration on Information Security
LG Uplus is enhancing its DX capabilities in order to become a customer-centric company, and is focusing its
efforts on the development of future growth drivers such as AI, big data and cloud technology, Based on
this, LG Uplus is expanding its business scope not only in the telecommunications sector, including
lifestyle, entertainment, and growth care platforms, but also in various other fields such as B2B new
businesses.
in the increasingly advanced environment, the value of information has become more important, and security
incidents are recognized as critical factors that determine a company's competitiveness and survival.
Therefore, all employees must have a deep understanding of the importance of information security and make
it a part of their daily activities.
The management is prioritizing the important information protection, including personal data, as a key
management task that enhances customer value. All employees and executives should be aware that information
security is an essential competitiveness factor for the continuous growth of the company.
Therefore, please strictly comply with the following five principles of information security.
1. All employees must comply with relevant laws and internal regulations and guidelines, such as the
information and Communications Networks Act and the Personal Information Protection Act.
2. All company information, including personal information, should be reconized as important assets and must
be managed and protected securely.
3. The level of individual security awareness should be improved through information securit education and
training.
4. Compliance with security requirements should be continuously reviewed to minimize the risk of security
incidents.
5. In the event of a security incident, it is necessary to comply with the company's response procedures and
to establish and implement measures to prevent recurrence.
Hyeon Sik Hwang, CEO of LG Uplus
Privacy Policy
LG Uplus guarantees the rights of information subjects according to the privacy protection laws. We comply
with the Privacy Protection Act and the Act on
Promotion of Information and Communications Network Utilization and Information Protection and establish and
disclose the ‘Privacy Policy’ following the
Standards for Technical and Administrative Measures for Protection of Privacy and the Privacy Policy.
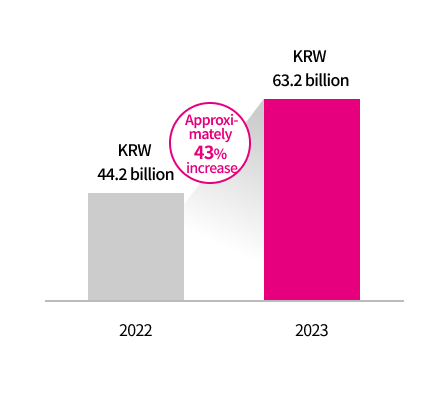
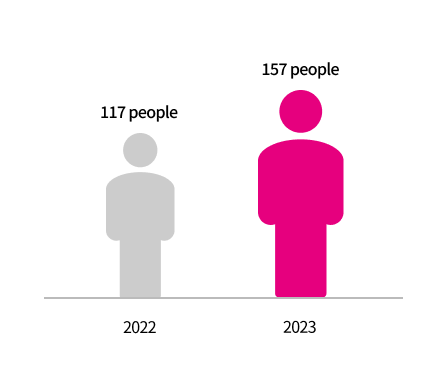
Information Security Investment
LG Uplus is trying to establish a safe and reliable information security and personal information protection
system by expanding investment and
dedicated personnel in the information security and personal information protection fields among information
technology fields.
Information Security and Privacy Protection Certification
LG Uplus has obtained certification related to information security and personal information protection such
as ISO27001, ISMS, and
ISMS-P, and operates an advanced information protection system.
Response Procedures for Security Incidents
Depending on the cause/type of security incidents such as DDoS attacks, Personal information leakage, etc.,
we have established and are operating a
response system that completes from identification of the
incident to notification to the customer within 24 or 72 hours. This allows us to quickly
recognize
and respond to damages.
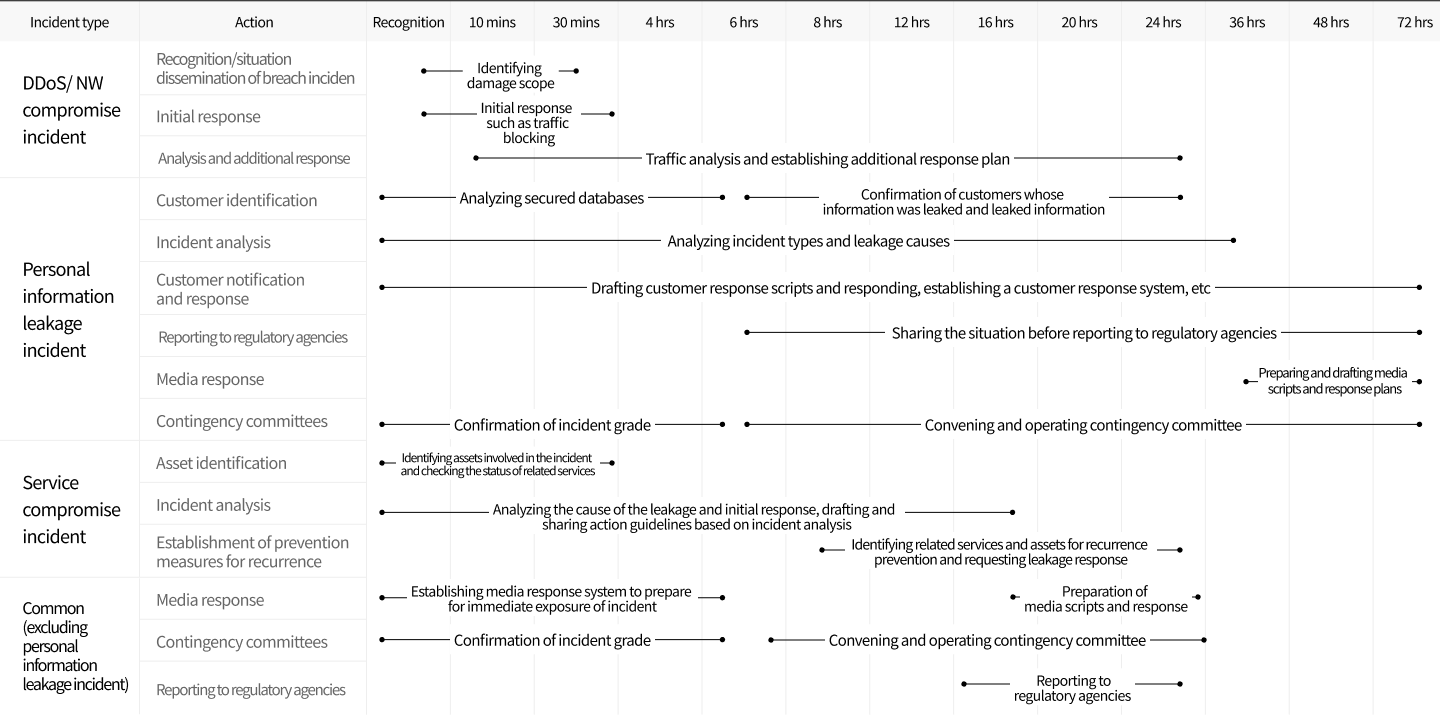
-
Incident type : DDoS/ NW compromise incident
Action
- Recognition/situation dissemination of breach Incident : Identifying damage scope(Recognition ~ within 30 mins)
- Initial response : Initial response such as traffic blocking ( Recognition ~ within 30 mins)
- Analysis and additional response : Traffic analysis and establishing additional response plan ( 10 mins~ within 24 hrs) -
Incident type : Personal information leakage incident
Action
- Customer identification : Analyzing secured databases(Recognition ~ within 6 hrs) , Confirmation of customers whose information was leaked and leaked information(6 hrs~ within 24 hrs)
- Incident analysis : Analyzing incident types and leakage causes (Recognition ~ within 36 hrs)
- Customer notification and response : Drafting customer response scripts and responding, establishing a customer response system, etc (Recognition ~ within 72 hrs)
- Reporting to regulatory agencies : Sharing the situation before reporting to regulatory agencies (6 hrs~ within 72 hrs)
- Media response : Preparing and drafting media scripts and response plans (36 hrs ~ within 72 hrs)
- Contingency committees : Confirmation of incident grade (Recognition ~ within 6 hrs), Convening and operating contingency committee (6 hrs ~ within 72 hrs) -
Incident type : Service compromise incident
Action
- Asset identification : Identifying assets involved in the incident and checking the status of related services (Recognition ~ within 30 mins)
- Incident analysis : Analyzing the cause of the leakage and initial response, drafting and sharing action guidelines based on incident analysis (Recognition ~ within 16 hrs)
- Establishment of prevention measures for recurrence : Identifying related services and assets for recurrence prevention and requesting leakage response (8 hrs ~ within 24 hrs) -
Incident type : Common (excluding personal information leakage incident)
Action
- Media response : Establishing media response system to prepare for immediate exposure of incident(Recognition ~ within 6 hrs), Preparation of media scripts and response(16 hrs ~ within 24 hrs)
- Contingency committees : Confirmation of incident grade(Recognition ~ within 6 hrs), Convening and operating contingency committee(6 hrs ~ within 24 hrs)
- Reporting to regulatory agencies : Reporting to regulatory agencies(16 hrs ~ within 24 hrs)
For more details, please refer to LG U+'s Sustainability Report.